THE ONLINE GAMING INDUSTRY: PROTECTING DATA INSIDE OUT
Jan 23, 2017
The worldwide online gaming industry is worth over £33B and expected to grow 10% year on year going forward. With more money flowing into online gaming and the continual global evolution of cyber-attacks, businesses that develop or operate betting platforms online and traditional casinos, become part of a lucrative eco-system that is a prime target to cyber criminals.
Breaches experienced in the online gaming industry are not news, however they’re often underreported since their impact on consumers can cause non-reversible reputation damage. Some of the most well-known breaches in the industry were the hack that affected Paddy Power which saw over 600K user accounts compromised and more recently the compromise of the UK’s national lottery (Camelot) seeing over 26K compromised accounts.
GPDR, regulations, PCI – where to start?
One of the current hottest topics discussed in businesses that hold personal data is the upcoming general data protection regulation (GDPR) which will come into effect 25th of May 2018. GDPR has created a sense of urgency with businesses realising the consequences of a data breach with enforced fines of €20M or %4 of the global annual turnover.
The online gaming industry is regulated where online gaming operators and vendors must adhere to regulations in their jurisdiction, as well as often conform to security standards like PCI (Payment Card Industry) if they hold or process credit card data. However, having different regulations that pose inconsistent penalties still sees breaches occurring and the penalties often criticised as being too low (e.g. Paddy Power breach saw a penalty of £280K against three hours trading value). Similar conditions in other industries finally resulted in GDPR which puts all personal data in focus and attaches substantial penalties in case a breach occurs – this forces all businesses that hold personal data to take a leap and keep up with the upcoming regulation.
Considering all the above, online gaming businesses often find it hard to embark in a Security Improvement Program (SIP), not due to lack of information on security or understanding the need for it, but mainly due to lack of structure or best practice required for a SIP; often online gaming businesses are willing and see value in a SIP while keeping customer experience intact and the momentum of innovation, but often ask “how do we do it right?”.
Choosing the approach for a Security Improvement Program
The practical methodology seen to improve security regardless of the industry is to work against a high-level baseline that represents the fundamental approach for a SIP; within that approach each of the tiers can adapt to the specific needs and environment of the business.
The high level approach for improving security is comprised of three main tiers for a SIP and holding the essence that security should be prioritised inside out; first is business’ core – its immediate assets which includes adhering to regulations, second consider the business’ partners access into the business, and last are the business consumers – this doesn’t refer to the consumer data but the actual actions taken on the consumer side against the business assets, like the gaming platform, that may be fraudulent, for e.g. stolen gaming credentials.
It’s important to note that each of the tiers is as important as the other tiers- the approach of securing the business ‘inside out’ prioritises taking actions and strengthening the core of the business first, considering security technology, people and process to lay a healthy foundation for the other tiers, if done otherwise it could result in different complications for e.g. in certain circumstances the core of the business can be left exposed to attacks by having technology, people and processes put on external tiers that may block the internal tier from providing sufficient security, or another scenario could be having a redundant security technology implemented in external tiers that could be achieved by a technology in the internal tier.
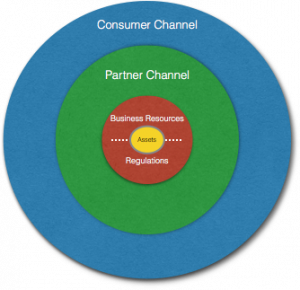
The Core (red):
- SIP for all assets owned by the business and their security on the network
- SIP to adapt to regulation requirements: GDPR, PCI, local jurisdiction etc.
The Middle tier (green):
- SIP for assets accessed by partners and 3rd party vendors
The outer tier (blue):
- SIP for gaming platform consumers
In the next blog, we’re going to look at the specific attacks gaming industry is experiencing and match them with the different SIP tiers – this will allow the gaming business to gain insights on the type of threats to put in focus when forming a SIP at the highest level, in addition we will focus on the core and partner tiers and describe an approach for a SIP to be best positioned against a potential data breach in the gaming industry.




