ONLINE GAMING – ASSESSING AND PRIORITISING CYBER DEFENCE CONTROLS
Feb 06, 2017
In a previous blog, we started mapping threats that are prevalent in the Gaming threat landscape to the different business channel tiers, in this blog we’re going to describe an approach to protect the Core and Middle tiers of the business against breaches.
Embarking on a Security Improvement Program (SIP) for the Core and Middle tier is an essential task that aims to protect all the core business assets from a cyber security breach, as well as recognise the risks posed by the partner channel to these assets. In this blog, we’ll describe a protection method that uses an algorithm which prioritises the security controls the business needs to focus on to maxmise its threat protection.
We are not going to work against an existing standard, however we will utilise a multitude approach that merges attack models and best practice defence models to offer best practice guidance; While working solely against some standards like PCI, HIPAA, CIP and others is possible (they’re often required by regulators), they have been criticised lately to hold a dated approach and should evolve to match-up with today’s threat landscape. The methodology we’re going to describe is holding the notion that today’s threats require a new approach to successfully protect against them.
Getting real with cyber attackers
We described in previous blogs how being on the defence all the time is bound to break and how shifting the approach to the attacker’s perspective can help business be better positioned to prevent security breaches. Thinking like an attacker or a malicious insider is essential to protect against them and to ‘get real’ with attackers the business first needs to understand how they work; it doesn’t mean the business needs to understand how to execute such attacks technically utilising similar tools, tactics and procedures that adversaries do, although some business use these methods as part of red and blue team exercise, the goal is to better understand the principals of an attack from the adversary’s perspective and adapt the business’ protection to that.
The principle steps that can lead to a breach
Adversaries, as well as insiders such as business employees are people and as people they should take actions that can lead to a data breach, the principal number of steps needed to successfully cause a breach is called the ‘kill chain’ – these actions will often be commenced sequentially and progress ‘blow by blow’ until complete and impact data.

Applying defence to the offensive security model
While understanding how the kill chain is a good start and represents the adversary’s side, it needs to be applied and translated into tangible defence mechanisms that the business could use, this is where best practices comes in. While there are many best practice guides and frameworks on applying defence, most of them focus on defence only without directly paralleling security controls to the offensive side represented by the kill chain. It’s also good to keep in mind that the ‘offensive side’ might be an internal trusted resource like an employee or a partner, usually employees or partners benefit from direct access to data which increases risk, unlike the adversary that needs to advance through the stages to gain control of data, the employee only needs to jump through one.
Our approach to Cyber Defence takes the kill chain model and parallels it to security controls per the established framework of SANS top 20 Critical Security Controls; each security control in the framework is translated to a tangible security control or process which is then built into and measured against the kill chain – using this approach to conduct a Cyber Defence Assessment can allow the business to gain unparalleled visibility to its position against how breaches come to play in practice.
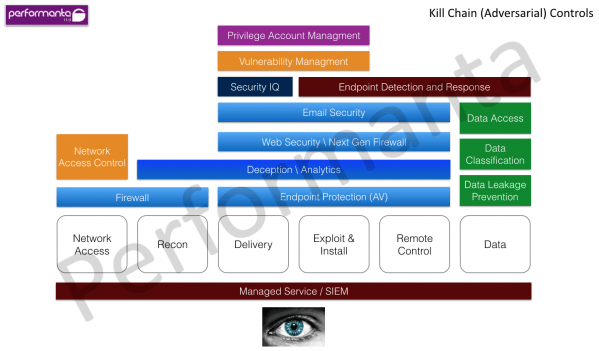
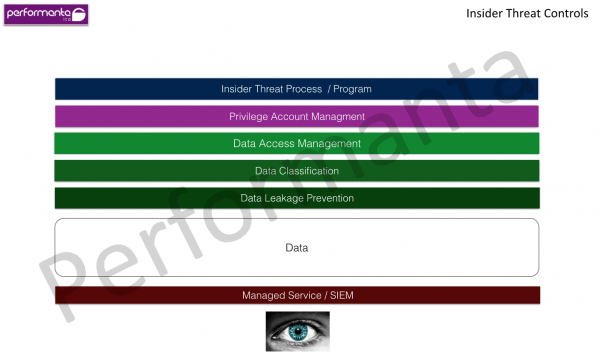

Prioritizing security focus areas – not all controls are equal
One of the challenges of choosing an established security framework like the SANS top 20 is that while there’s a hefty amount of information and controls, there’s no way to globally prioritise which controls should be in focus to maximise defences against a breach. The CXO is often challenged to priorities controls, most of the time the ongoing burning issues will gain the most focus, however, the CXO should also keep in mind the burning issues of tomorrow by considering attack chain vectors that may come to play and compromise data, as well as consider ’silent failures’ where security controls are evaded with no alarms are going off.
Since not all controls are equal and each business is uniquely positioned, surveying security controls by mapping them to the kill chain also gives the business the visibility which controls need to be prioritised to gain maximum protection against the kill chain – this is where an algorithm that takes the impact of a security control into account helps make global security control prioritisation, for e.g. web security gateway is a control that protects against three stages in the kill chain which needs to be factored in to help the business maximise their defence each control investment, this can help manage security budgets more effectively while seeing improvement in cyber defences.
The next image captures the results of a Cyber Defence Assessment per the method described above to a client in the retail business. The security controls for the adversarial and the insider threat are shows (blue), as well as the controls that will benefit protection against the kill chain and insider threat the most (red).
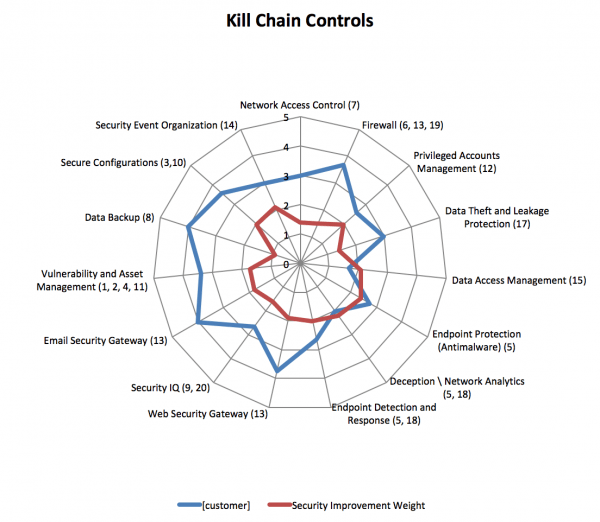
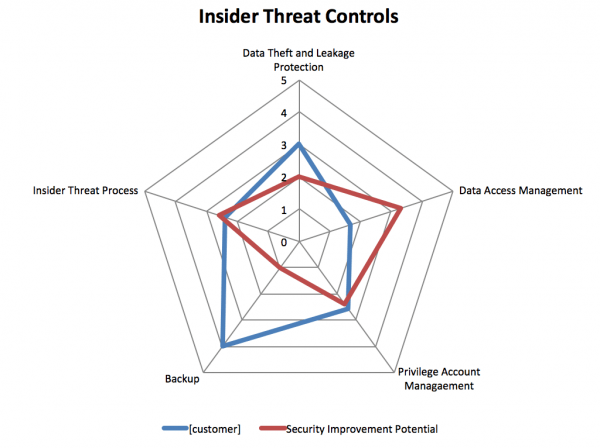
In this blog we described a practical approach to protect the business core and middle tiers against adversarial and insider threats, this approach to Cyber Defence allows the business to map critical security controls against the kill chain and by that gives the business a tool that can help gain true visibility of their security posture parallel to the way breaches occur, as well as prioritises security controls by calculating how effective the business’ security controls are against the kill chain.




